Use DNF to Maintain Security on Oracle Linux
Introduction
The following tutorial provides practical examples of using the Dandified YUM (DNF) package manager on Oracle Linux to apply maintenance and security updates. This tutorial is targeted at users of Oracle Linux 8 or later.
DNF downloads packages from enabled repositories for install and update actions. It performs automatic dependency resolution for packages and installs all packages needed to fulfill dependency requirements. DNF also includes integrated options for managing security and errata updates available for packages installed in Oracle Linux.
A security patch is an update to fix a specific vulnerability incorporating changes in source code. These security patches usually apply to particular software components.
A bug fix is the elimination of known software errors.
CVE is short for Common Vulnerabilities and Exposures. It is a list of publicly disclosed computer security flaws. A CVE refers to a security flaw where a CVE Numbering Authority (CNA) assigns a CVE ID number. Security advisories usually refer to at least one CVE ID, with a priority ranging from negligible through low, medium, high to critical.
Enterprise Linux denotes these specific updates as:
ELSA: Enterprise Linux Security Advisory patchesELBA: Enterprise Linux Bug Fix Advisory patchesELEA: Enterprise Linux Enhancement Advisory patches
Objectives
In this lab, you'll learn:
- The meaning of CVEs, ELSAs, and Bug Fixes
- To use DNF for installing security updates
- That package updates are cumulative and have dependencies
- To clean up old packages
What Do You Need?
- An Oracle Linux system.
Setup Lab Environment
Note: When using the free lab environment, see Oracle Linux Lab Basics for connection and other usage instructions.
Some of the dnf commands in this lab require the use of sudo to avoid the following message: Error: This command has to be run with superuser privileges (under the root user on most systems).
Open a terminal and connect via SSH to the ol-node01 instance if not already connected.
ssh oracle@<ip_address_of_instance>Confirm hostname and version of Oracle Linux.
hostnamectl
List All Available Security Packages for the System
List a summary of the types and totals of available errata.
dnf updateinfo summaryList all the errata that are available for the system.
dnf updateinfo listThe example output shows the enabled repositories followed by each update. The available errata are sorted in order of their IDs and identify their types.
Severity/Sec: Priority/Security patchbugfix: Bug fixenhancement: Feature enhancement
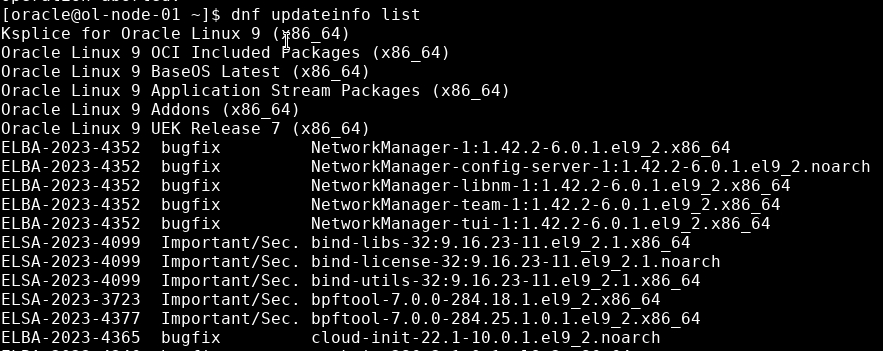
List detailed information on each of the available errata.
dnf updateinfo infoExample output of errata showing the dependencies, if any.
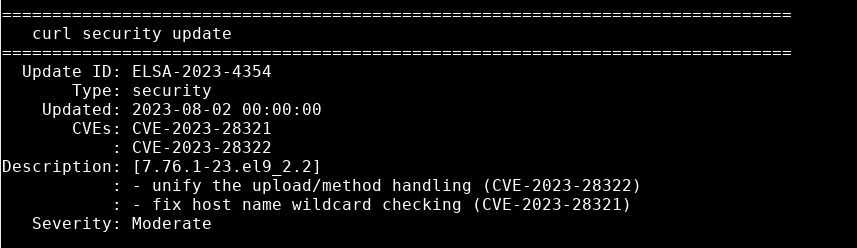
Filter the List of Security Updates
You can limit the output to specific types by including various arguments after the
listkeyword.List all security updates installed on the host, specify the arguments
security --installed.dnf updateinfo list security --installedList all available security updates not installed on the host, specify the arguments
updates security.dnf updateinfo list updates securityList the security errata by their Common Vulnerabilities and Exposures (CVE) IDs, specify
cvesas an argument.dnf updateinfo list cvesList the bugfixes, specify
bugfixas an argument.dnf updateinfo list bugfixList the available security upgrades, specify
secas an argument.dnf updateinfo list secList the security patches according to severity level, by specify
--sec-severity=as an argument and appending the severity.dnf updateinfo list --sec-severity=ImportantThese are the available severity levels:
CriticalImportantModerateLow
List the security errata for a specific CVE, specify the keyword
--cvefollowed by a CVE ID as an argument.dnf updateinfo list --cve CVE-2023-1998List the information for a specific Advisory, specify the keyword
--advisoryfollowed by an Advisory ID as an argument.dnf updateinfo list --advisory ELSA-2023-3723dnf updateinfo list --advisory ELBA-2023-3732
Detailed Information of Security Updates
The
dnf updateinfo infocommand lists detailed information for a specific errata. You can limit the output to particular types by including various arguments after theinfokeyword.List detailed information for a specific Advisory, specify
--advisoryfollowed by an Advisory ID as an argument.dnf updateinfo info --advisory ELSA-2023-3723dnf updateinfo info --advisory ELBA-2023-3732List the detailed information for a specific CVE, specify
--cvefollowed by a CVE ID as an argument.dnf updateinfo info --cve CVE-2023-1998
Update Packages
The
dnf updatecommand updates packages to the latest version. You can limit the output to a specific errata by including various arguments after theupdatekeyword. You can implement the updates by respondingyat the prompt.Update packages for a specific CVE or erratum, specify the keyword and argument
--cve CVE ID.sudo dnf update --cve CVE-2023-1998The output from the update and upgrade commands shows four sections:
InstallingUpgradingInstalling dependenciesInstalling weak dependencies
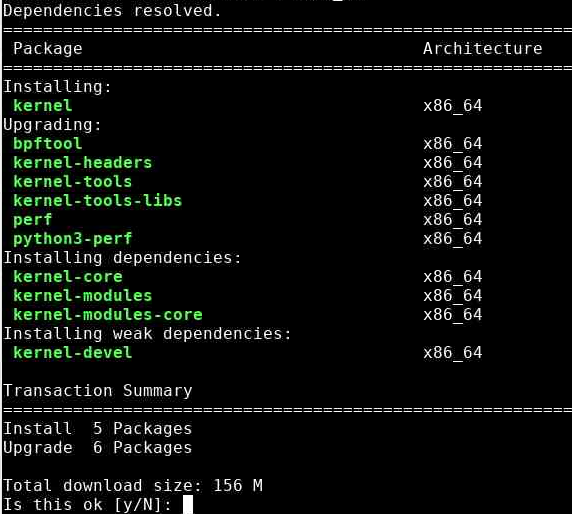
Update packages for a specific Advisory, specify the keyword
--advisoryfollowed by an Advisory ID as an argument.sudo dnf update --advisory ELSA-2023-3723Update all packages to the latest versions for which security-related errata are available, even if those packages include bug fixes or new features but not security errata.
sudo dnf --security update --assumenoThe
--assumenooption automatically answers no for all questions. This aborts the operation allowing the texting of furtherdnf --securityoptions.Update all packages to the latest versions that contain security errata while ignoring any newer packages that don't have security errata.
sudo dnf --security upgrade-minimal --assumenoUpdate all kernel packages to the latest versions that contain security errata.
sudo dnf --security upgrade-minimal kernel* -yThe
-yoption automatically answers yes for all questions and, therefore, automatically applies the requested security packages.Update a system to use the latest packages that are available.
sudo dnf upgradeTwo dnf commands are available to update all packages:
dnf updateanddnf upgrade. Both commands install all available updates, butdnf updateautomatically runsdnf upgrade, sodnf upgradeis preferred.
Cleanup
DNF stores and persists packages it downloads on disk as part of an install action. Occassional clean up is essential to reduce the amount of used disk storage.
Running the dnf clean command removes the cache and files. You can limit the clean up to a specific area by including various arguments after the clean keyword.
Remove all cache files generated from the repository metadata, specify the keyword
dbcache.sudo dnf clean dbcacheEmpty the cache directory for the enabled repositories of all cached packages, specify the keyword
packages.sudo dnf clean packagesSpecify the keyword ' all ' to clear all cached files from all enabled repositories.
sudo dnf clean all
For More Information
See other related resources: