Integrate LDAP User Management with Oracle Linux Automation Manager
Introduction
Oracle Linux Automation Manager enables administrators to integrate LDAP for user management alongside the existing internal RBAC (Role-Based Access Control) source. Once configured, users logging in with an LDAP account automatically generate an Oracle Linux Automation Manager account and get assigned to a standard user or administrator organization.
Objectives
In this tutorial, you'll learn how to:
- Create and configure accounts and groups in LDAP
- bind account
- user account
- superuser group
- system_auditor group
- Configure Oracle Linux Automation Manager to use LDAP
- Verify LDAP access
- Enable LDAPS
Prerequisites
- A system with Oracle Linux Automation Manager installed.
- An available LDAP server, such as the open-source FreeIPA identity management server.
Deploy Oracle Linux Automation Manager
Note: If running in your own tenancy, read the linux-virt-labs GitHub project README.md and complete the prerequisites before deploying the lab environment.
Open a terminal on the Luna Desktop.
Clone the
linux-virt-labsGitHub project.git clone https://github.com/oracle-devrel/linux-virt-labs.gitChange into the working directory.
cd linux-virt-labs/olamInstall the required collections.
ansible-galaxy collection install -r requirements.ymlUpdate the Oracle Linux instance configuration.
cat << EOF | tee instances.yml > /dev/null compute_instances: 1: instance_name: "olam-node" type: "control" 2: instance_name: "ipa-server" type: "server" use_freeipa: true olam_type: single EOFCreate an inventory file.
cat << EOF | tee hosts > /dev/null localhost ansible_connection=local ansible_connection=local ansible_python_interpreter=/usr/bin/python3.6 EOFDeploy the lab environment.
ansible-playbook create_instance.yml -i hosts -e "@instances.yml"The free lab environment requires the extra variable
ansible_python_interpreterfor localhost because it installs the RPM package for the Oracle Cloud Infrastructure SDK for Python. The location for installing this package is under the system's default Python modules based on your version of Oracle Linux. Using an inventory variable avoids impacting the plays running on hosts other than localhost.The default deployment shape uses the AMD CPU. You can change the shape of the instances by passing a new shape variable definition on the command line.
For example:
-e instance_shape="VM.Standard3.Flex"Similarly, the default version of the Oracle Linux image uses the variable
os_versiondefined in the `default_vars.yml file. You can modify this value by passing the Oracle Linux major version on the command line.For example:
-e os_version="9"Important: Wait for the playbook to run successfully and reach the pause task. At this stage of the playbook, the installation of Oracle Linux is complete, and the instances are ready. Note the previous play, which prints the public and private IP addresses of the nodes it deploys.
Verify the IPA Server Exists
Open a terminal and connect via SSH to the ipa-server instance.
ssh oracle@<ip_address_of_node>Verify the IPA service is running.
sudo systemctl status ipa.serviceThe ipa.service leverages the
ipactlcommand, which simultaneously starts or stops all the individual components.Set the terminal localization settings.
This setting is a requirement of the
ipactlcommand.export LC_ALL="C.UTF-8"Check the status using the IPA server control interface.
sudo ipactl statusAll the listed components must be running for the IPA server to function correctly.
Create a Bind Account
The bind account is a system account that allows read-only access to the entire LDAP structure. Using a bind account rather than a regular user account prevents access into any other systems, and it doesn't own any files. Further, the bind account has no special rights and cannot write any data in the IPA LDAP server.
Create an update file.
According to the ipa-ldap-updater manual page, the update file describes an LDAP entry to add or modify, along with a set of operations to perform on that entry.
tee olam-binddn.update << EOF dn: uid=olam-bind,cn=sysaccounts,cn=etc,dc=lv,dc=vcn,dc=oraclevcn,dc=com default:objectclass:account default:objectclass:simplesecurityobject default:uid:olam-bind only:userPassword:olamPassword123 only:passwordExpirationTime:20380101000000Z only:nsIdleTimeout:0 EOFSelect a strong and secure password for the bind user account and a reasonable uid. The userPassword and uid above are for demonstration purposes only within the free lab environment.
Import the update file into the IPA server.
sudo ipa-ldap-updater olam-binddn.updateVerify the new bind account exists.
ldapsearch -D 'cn=Directory Manager' -x uid=olam-bind -WEnter the password for the Directory Manager account when prompted.
The password is
DMPassword1in the free lab environment.Example Output:
[oracle@ipa-server ~]$ ldapsearch -D 'cn=Directory Manager' -x uid=olam-bind -W Enter LDAP Password: # extended LDIF # # LDAPv3 # base <dc=lv,dc=vcn,dc=oraclevcn,dc=com> (default) with scope subtree # filter: uid=olam-bind # requesting: ALL # # olam-bind, sysaccounts, etc, lv.vcn.oraclevcn.com dn: uid=olam-bind,cn=sysaccounts,cn=etc,dc=lv,dc=vcn,dc=oraclevcn,dc=co m objectClass: account objectClass: simplesecurityobject objectClass: top uid: olam-bind userPassword:: e1BCS0RGMl9TSEEyNTZ9QUFBSUFPTjJrZ295RVBRcmFtWkFydE5kRllNOVlkcmp UK2pVMkgwTm5qUUpxbHpJTUNxSUJOUXp4Z1F5emVqdk02Nk5jL2ZXMVNvelUyaGUwZDFJenFMN2Fk aExTaWFnc1kzVVFTbnBxL3RUdUo3VnBvU05GaXFpQWJTWktrcGZwR0REM0lNdCtKRWt1T2NBRk94d mFwS2tTUC9KS1FYUVprcGRjbzF0TlZDNHkzNEE4cFQ2UGtWM0pFcm4zdUNkdkVGZ2ZIM1Y4QWxiaG pQcm9HWU50aTdrMXRrM0ZkdFI0VlNGWW96SUcra2tUTkt1OE9tYVl3YXp6ZlV5VHBxeFFEMnBxRy9 XYmxBdW02OURNcDA2RzVBZUJzRGlYOWpDWkZrenNwbllKQXdiQ015MTFXVXI0TFB5VzByejNac2V0 SmE0dU9yS2NmOWhCZWpBV3NiRlNhQVR0MTU4V2FtN3Q2S21wNXU5em1yTm9oMVRCeEdqaG5Mb3dJN kdjcDF4a2p2VkNsYmhVSkQxZTRqS0lzTFJHc3JOclRKN3R0MitpbXZtSlRtR1FkRllsb1dr # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
Create a User
Oracle Linux Automation Manager creates a default admin user during installation. You'll make an LDAP user, who will get assigned the same privileges.
Manually authenticate to the IPA server by obtaining a Kerberos ticket.
kinit adminEnter the IPA server's pre-defined admin account password.
The password is
ADMPassword1in the free lab environment.Create a user in the IPA server.
ipa user-add olam_admin --first=OLAM --last=Administrator --passwordPass the user's login, first name, and last name to the
ipa user-addcommand. When saving these details to the directory, IPA automatically converts the entire user login to lowercase, making mixed-case usernames impossible.Enter and verify a password of your choosing at the prompt for the olam_admin account.
Verify the user exists by listing all the IPA server accounts.
ipa user-findThe results show the default IPA server admin account and the newly created olam_admin.
Create a Group
Oracle Linux Automation Manager has three user types, of which two translate to LDAP groups you need to create. These groups are for the System Administrator and System Auditor types.
Create the administrator group.
ipa group-add olam_administratorsCreate the auditor group.
ipa group-add olam_auditorsAdd the new user to the administrator group.
ipa group-add-member olam_administrators --users=olam_adminThat completes the minimally required steps on the IPA server.
Close the open session to the IPA server.
exit
Install the LDAP Client Tools
Oracle Linux Automation Manager does not install the suite of OpenLDAP applications and development tools by default. Administrators can use these tools to access and modify LDAP directories from the terminal to help test their configuration.
Connect via SSH to the olam-node instance using the existing terminal.
ssh oracle@<ip_address_of_node>Install the OpenLDAP tools package.
sudo dnf -y install openldap-clientsConnect and search the LDAP server.
ldapsearch -D uid=olam_admin,cn=users,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=com -W -H ldap://ipa-server.lv.vcn.oraclevcn.com:389-D: is the Distinguished Name (DN) to bind to the LDAP directory-W: prompts for simple authentication-H: specifies the LDAP server's URI, which consists of the protocol, host, and port only
Enter the password for the
olam_adminuser at the prompt.The output returns the search results if the connection is successful.
Close the terminal session.
exit
Log Into the Oracle Linux Automation Manager Web UI
Configure an SSH tunnel to the olam-node instance using the existing terminal.
ssh -o ExitOnForwardFailure=yes -f -L 8444:localhost:443 oracle@<ip_address_of_node> sleep 300-o ExitOnForwardFailure=yes: waits for all remote port forwards to establish successfully-f: runs the SSH tunnel in the background-L: creates the tunnel on port 8444 on the local system and 443 on the remote systemsleep 300: keeps remote tunnel open for 5 minutes, waiting for an established connection before automatically closing
Open a web browser and enter the URL.
https://localhost:8444Note: Approve the security warning based on the browser used. Click the Advanced button for the Chrome browser and then the Proceed to localhost (unsafe) link.
Log into Oracle Linux Automation Manager Web UI.
Use the Username
adminand the Passwordadminin the free lab environment.
After logging in, the Web UI displays.
Open the LDAP Settings
A user with the System Administrator privilege uses the Settings page of the Oracle Linux Automation Manager Web UI to add alternative Authentication settings, such as LDAP.
Click Settings at the bottom of the navigation menu to display the Settings page.
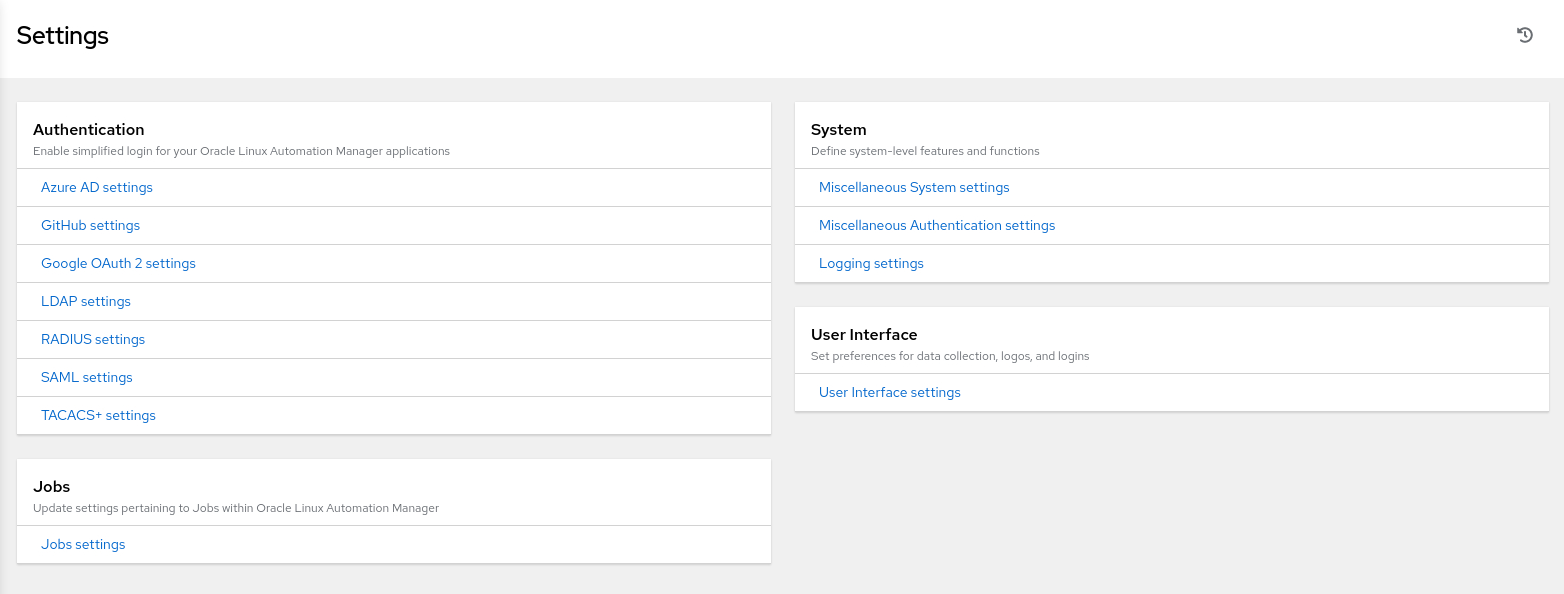
This page gives access to alternative Authentication settings you'll use to configure access to the LDAP server.
Click the LDAP settings link under the Authentication section.
Clicking this link displays the Default LDAP server configuration page. Beyond the default LDAP server, Oracle Linux Automation Manager allows you to configure five additional LDAP sources.
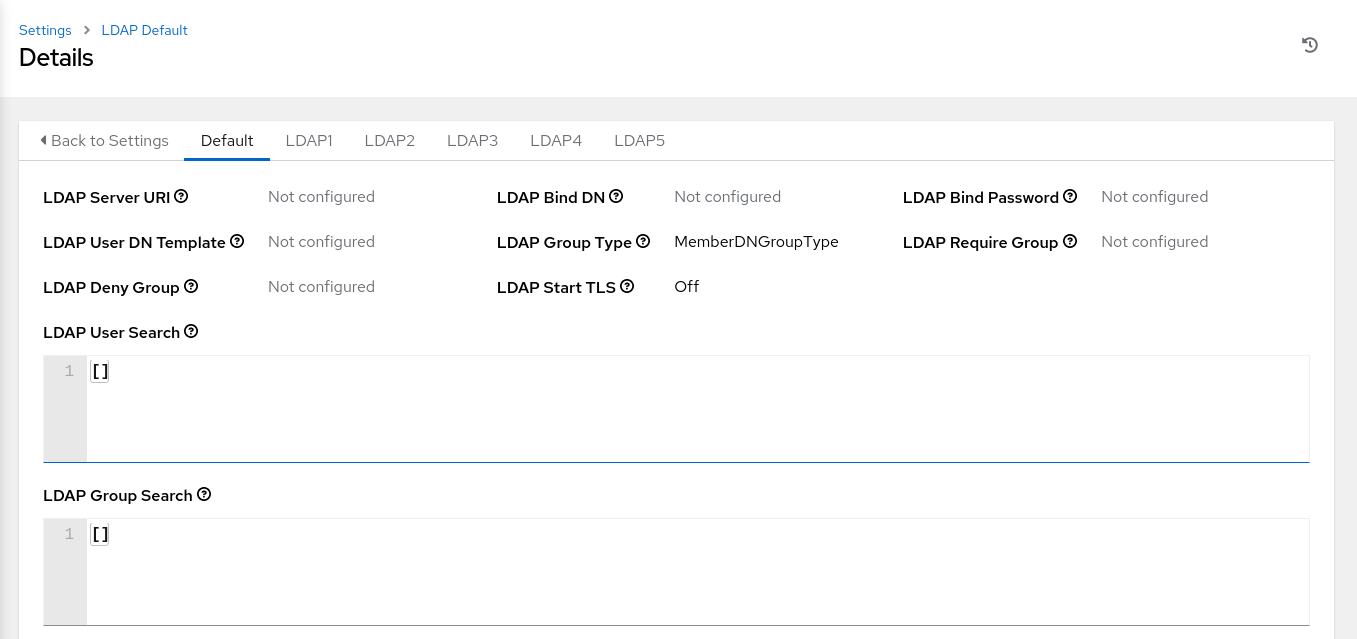
Edit the Default LDAP Setting
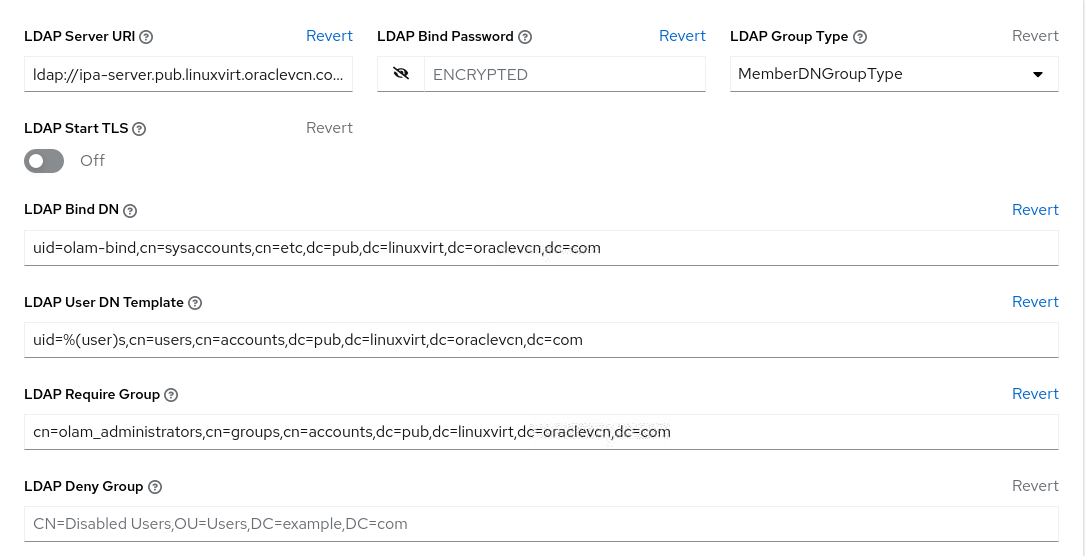
Scroll to the bottom of the Default Details page and click the Edit button.

The page refreshes and now allows editing of the different fields. Using
Ctrl+Vis recommended when pasting your entries into the various fields in the free lab environment.Enter the LDAP server address in the LDAP Server URI field.
ldap://ipa-server.lv.vcn.oraclevcn.com:389Enter the password for the bind user in the LDAP Bind Password field.
The password is
olamPassword123in the free lab environment.olamPassword123Oracle Linux Automation Manager encrypts the password field after saving the configuration changes. You can still edit the LDAP Bind Password field, but the Web UI no longer shows the initial password entered.
Click and select the group type from the LDAP Group Type drop-down list of values.
In the free lab environment, the LDAP Group Type defaults to MemberDNGroupType, which you'll use with our LDAP server.
The LDAP Group Types that Oracle Linux Automation Manager supports uses the django-auth-ldap-library .
Each LDAP Group Type may take different parameters, so look at the
initclasses in the django_auth_ldap upstream documentation to determine the expected parameters.Enter the Distinguished Name (DN) in the LDAP Bind DN field for the LDAP user that Oracle Linux Automation Manager uses to connect or bind to the LDAP server.
Use the previously created olam-bind user account.
uid=olam-bind,cn=sysaccounts,cn=etc,dc=lv,dc=vcn,dc=oraclevcn,dc=comEnter the key that stores the user's name in the LDAP User DN Template field.
uid=%(user)s,cn=users,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=comEnter the group distinguish name in the LDAP Require Group field to allow users within that group access to Oracle Linux Automation Manager.
cn=olam_administrators,cn=groups,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=comThe Edit Details page should look like the screenshot in the free lab environment at this stage.
Enter the location to search for users when authenticating in the LDAP User Search field.
[ "cn=users,cn=accounts,dc=lv,dc=1inuxvirt,dc=oraclevcn,dc=com", "SCOPE_SUBTREE", "(uid=%(user)s)" ]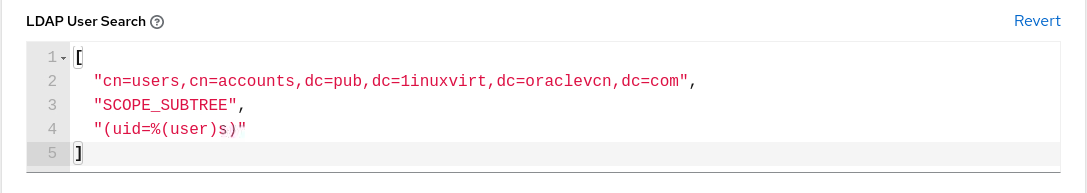
In the LDAP Group Search field, enter which groups to search and how to search them.
[ "cn=groups,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=com", "SCOPE_SUBTREE", "(objectClass=groupofNames)" ]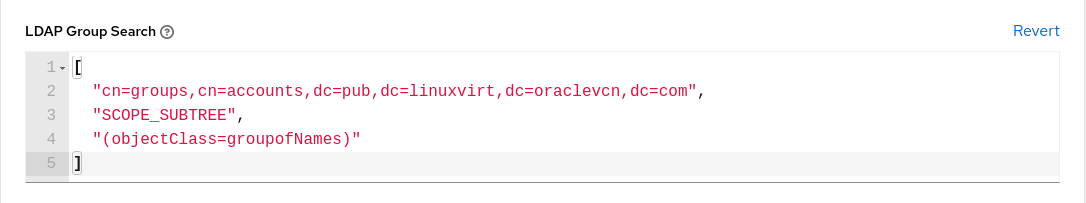
Enter the user attributes in the LDAP User Attribute Map text field.
{ "email": "mail", "first_name": "givenName", "last_name": "sn" }When retrieving users, Oracle Linux Automation Manager gets the user by the last_name from the sn key.
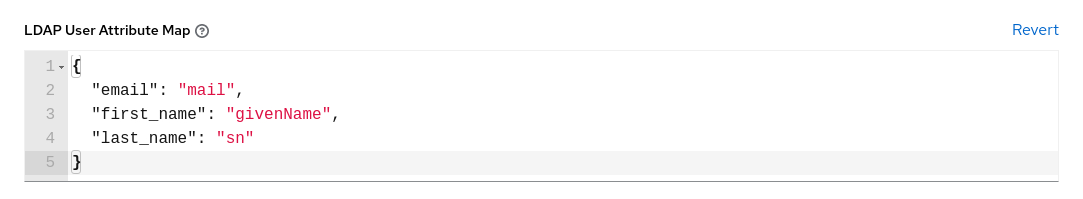
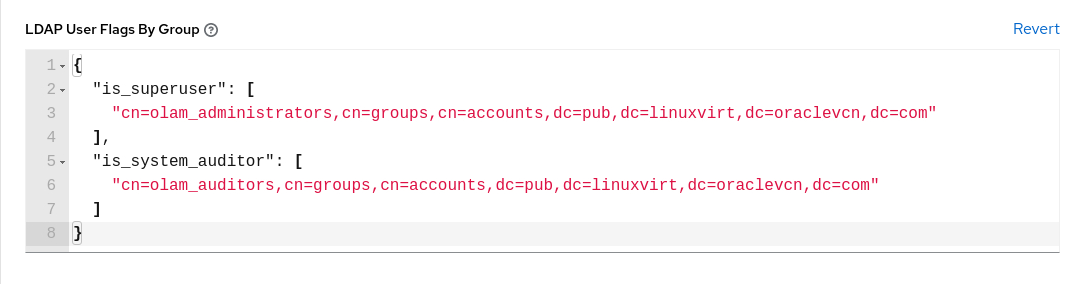
Enter the user profile flags in the LDAP User Flags by Group field.
These profiles assign the LDAP users as Superusers and Auditors.
{ "is_superuser": "cn=olam_administrators,cn=groups,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=com", "is_system_auditor": "cn=olam_auditors,cn=groups,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=com" }Oracle Linux Automation Manager alters the format of this field after saving the configuration to match the example shown.
Click the Save button when done.
Verify the Authentication Settings
After saving the LDAP settings, you should be able to log into Oracle Linux Automation Manager as an LDAP user.
Log out of Oracle Linux Automation Manager.
Click the admin user in the upper right corner of the Web UI and select Logout from the list of values.
Log in to Oracle Linux Automation Manager with the Username
olam_admin.Use the password you assigned to the user during account creation.
Click the Users menu item in the navigation menu.
Ensure the
olam_adminexists in the list of users.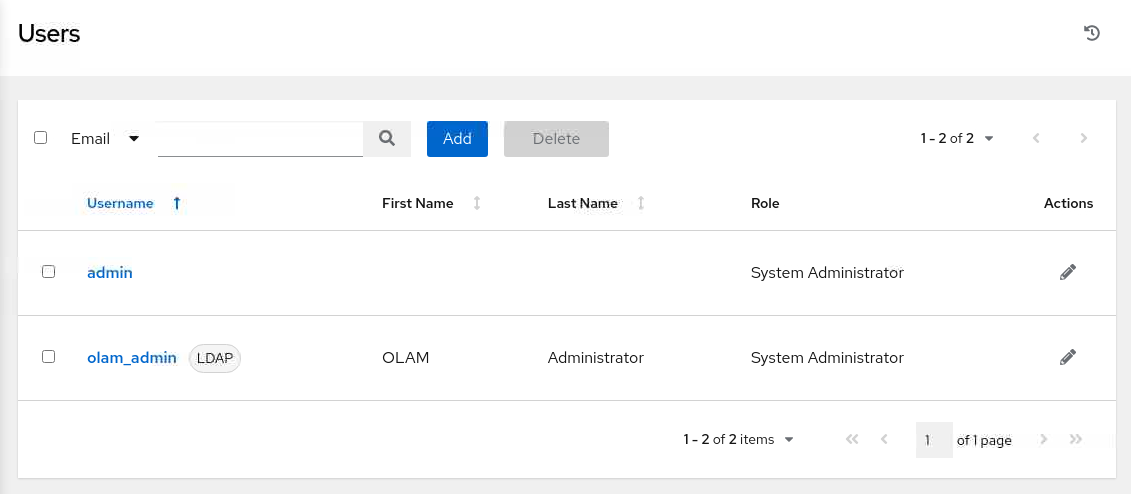
Important: Oracle Linux Automation Manager does not automatically sync users; instead, it creates and adds them during the user's initial login.
(Optional) Enable SSL/TLS
The IPA server installs a selfsign self-signed CA using certutil to generate certificates. These certificates allow testing SSL and TLS communication between the client and server. Production environments should use certificates signed by a trusted Certificate Authority (CA).
The IPA server's self-signed CA certificate is located in the /etc/ipa/ca.crt directory on the IPA server.
Switch to the open terminal session connected to the olam-node instance.
Copy the self-signed CA from the IPA server to Oracle Linux Automation Manager.
scp oracle@ipa-server:/etc/ipa/ca.crt ~/Type
oracleas the password andENTERif the terminal presents a password prompt in the free lab environment.Copy the self-signed CA certificate to the Oracle Linux Automation Manager server's Shared System Certificate directory.
sudo mv ~/ca.crt /etc/pki/ca-trust/source/anchors/ipa.crtChange the ownership on the certificate file.
sudo chown root.root /etc/pki/ca-trust/source/anchors/ipa.crtUpdate the system-wide trust store configuration.
sudo update-ca-trustTest connecting to the LDAP server with SSL.
ldapsearch -D uid=olam_admin,cn=users,cn=accounts,dc=lv,dc=vcn,dc=oraclevcn,dc=com -W -H ldaps://ipa-server.lv.vcn.oraclevcn.comSwitch back to the browser and, if necessary, log in to Oracle Linux Automation Manager as the
adminuser.Navigate to Settings and LDAP settings.
Scroll down and click the Edit button.
Either update the LDAP Server URI or LDAP Start TLS.
If you elect to update the LDAP Server URI, change the protocol from
ldap://toldaps://and the port from389to636.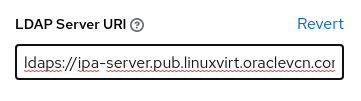
If updating LDAP Start TLS, toggle the switch to On.

Important: LDAPS with Oracle Linux Automation Manager only works when one of these options is enabled, not both. Therefore, if you update the URI, do not enable the toggle, and vice versa.
Scroll to the bottom of the page and click the Save button.
Log out of the Web UI.
Log in to Oracle Linux Automation Manager with the Username
olam_adminand the password you assigned during account creation.
Once logged in, you have confirmed the SSL/TLS communication between Oracle Linux Automation Manager and the LDAP server is working. If time permits, edit the LDAP settings again and try the other option.
Next Steps
Your Oracle Linux Automation Manager can now successfully authenticate its users against an external LDAP server, allowing central administration of the Web UI credentials and access control. Check out some of our other Oracle Linux Automation Manager training by visiting the Oracle Linux Training Station.